Why Cyber Security is Important to Prevent IT Outages
As technology continues to advance at an exponential rate, we are now more dependent on tech than ever before. However, along with all the benefits of this connectivity, there are also potential threats associated with using technological devices and online networks.
The rise in cybercrime has highlighted the need to focus on security and encryption strategies. Studies have shown that there were 2,365 cyberattacks in 2023, with 343,338,964 victims. Cyber threats and vulnerabilities can impact all types of organizations across a wide range of industries. Therefore, it is crucial for modern businesses to understand what cybersecurity is and the importance of effective cybersecurity strategies in the digital age.
In this article, we will answer key questions such as ‘What is a cyber attack?’, ‘What does cyber security do?’, ‘What are the types of cyber security?’ and more. We will also discuss emerging cybersecurity trends and the potential negative impact of a lack of security in today’s age.
What is Cyber Security?
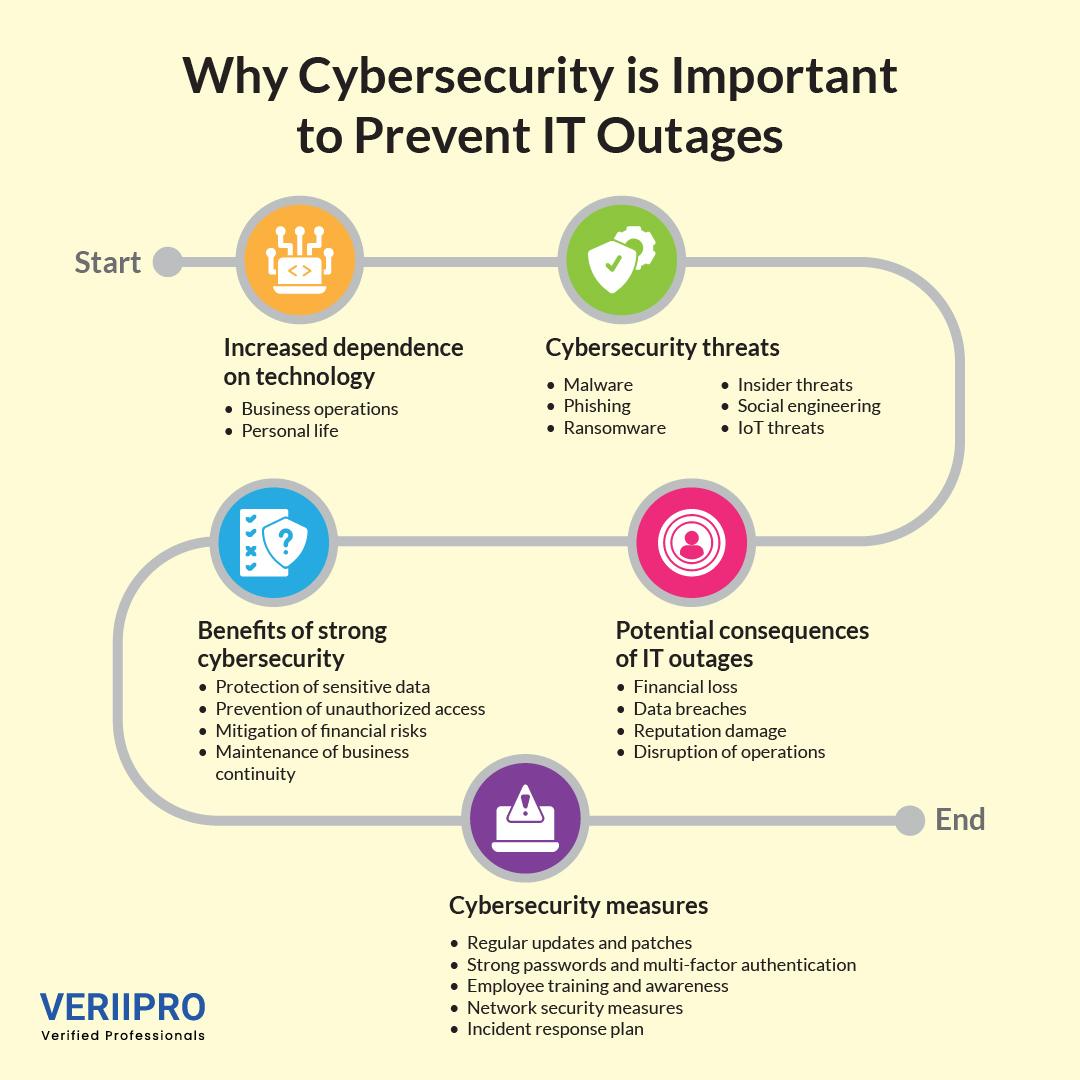
Cyber security is the protection and safeguarding of devices connected to the internet and online services from attacks and threats from cybercriminals, hackers, and spammers. It helps individuals and companies protect themselves and their sensitive data from potential threats, vulnerabilities, data breaches, ransomware attacks, phishing schemes, and potential financial loss.
As cyberattacks become increasingly sophisticated and advanced (with the rise of AI and social engineering that can overcome traditional security measures), cybersecurity is now more important than ever before.
Prioritizing cybersecurity is crucial for all modern organizations. It can help protect all categories of data and information from potential safety-related issues, including sensitive data, personally identifiable information (PII), intellectual property, health-related information, and more.
The Scale of the Cyber Security Threat
The impact of emerging cyber security threats is growing larger as technology continues to advance. These potential threats and vulnerabilities can have significant impacts on the profitability of large businesses, as well as lead to the theft of intellectual property, data breaches of sensitive corporate information, unexpected expenses, and damage to an organization’s reputation.
Data breaches and cyberattacks may also lead to lost customer trust, potentially driving customers away and leading to compliance-related fines. Therefore, it is crucial for businesses of all sizes to prioritize cybersecurity programs and initiatives to avoid this. A detailed and comprehensive security strategy and framework can help your business reduce the risk of data breaches and potential threats.
Why Is Cyber Security Important?
One security breach can lead to the exposure of the personal information of millions of individuals, customers, or employees. These types of breaches can have a significant financial impact on both your organization as well as the trust your consumers place in your services. Therefore, cybersecurity initiatives are extremely important for protecting your business from cybercriminals.
Staying up to date on cybersecurity trends and building strategies to protect your organization’s data ensures that your assets and services are protected against potential attacks and vulnerabilities.
Types of Cyber Threats
With recent tech advancements and emerging types of potential vulnerabilities, cyber threats can come in a variety of different forms. Understanding these types of cyber threats will allow your organization to proactively develop strategies to protect against them and develop best practices to avoid or address them.
1. Malware
Malware (malicious software) is a type of software intended to cause damage to a device, server, online network, or client. Malware may include potential cyber threats such as spyware, ransomware, trojans, viruses, or worms.
Once malware infiltrates a system, it can access, encrypt, or completely delete sensitive data, alter key computing functions, and even monitor user activity without consent.
2. Phishing
Phishing is the exchange of deceptive communication (usually through emails) that appears to come from a trustworthy and reliable source. However, these types of cyber threats are usually strategies to convince users to disclose their personal information to scammers. This includes data such as login credentials, credit card numbers, personal documents, and more. Phishing attacks usually lead to financial loss or identity theft.
3. Ransomware
Ransomware is a type of malware that encrypts a user’s information and then demands payment (usually in cryptocurrency) to decrypt it. These attacks can cripple organizations by compromising access to crucial data, information, and systems.
4. Insider Threats
Insider threats refer to cyber threats or data breaches that are orchestrated and led by individuals from within an organization. This includes employees, contractors, or partners. These stakeholders may intentionally or unintentionally compromise the security of organizational systems and processes by leaking sensitive information or data, mishandling mission-critical systems, or providing unauthorized access to third-party individuals.
5. Social Engineering
Social engineering is a psychologically-driven cyber threat that manipulates users into providing sensitive or confidential information, as well as undergoing actions that may compromise overall security. Common social engineering strategies include pretexting, spear-phishing, and baiting. These tactics involve sending highly personalized messages to individual users to gain access to their personal information.
6. IoT Threats
As the number of Internet of Things (IoT) devices used within an organization increases, so does the risk of a cyber attack. IoT devices usually lack stringent and comprehensive security measures, making them potential targets for attacks and threats. IoT threats can also provide hackers with access to larger and more important organizational networks and systems.
VeriiPro: Safeguard Cyber Security Through Your Next Role Today
Are you searching for your next job role in the cybersecurity field? VeriiPro can help!
Information security jobs are projected to grow by 32% by 2032. Our recruitment platform and job search tools are the perfect tools to help you find your dream position in cybersecurity. By collaborating with us and our team of experts, you can contribute to the cybersecurity of the perfect organization for you. We can help you find a job role that perfectly matches your needs and expectations.









