Securing America’s Data in the Age of Quantum Threats
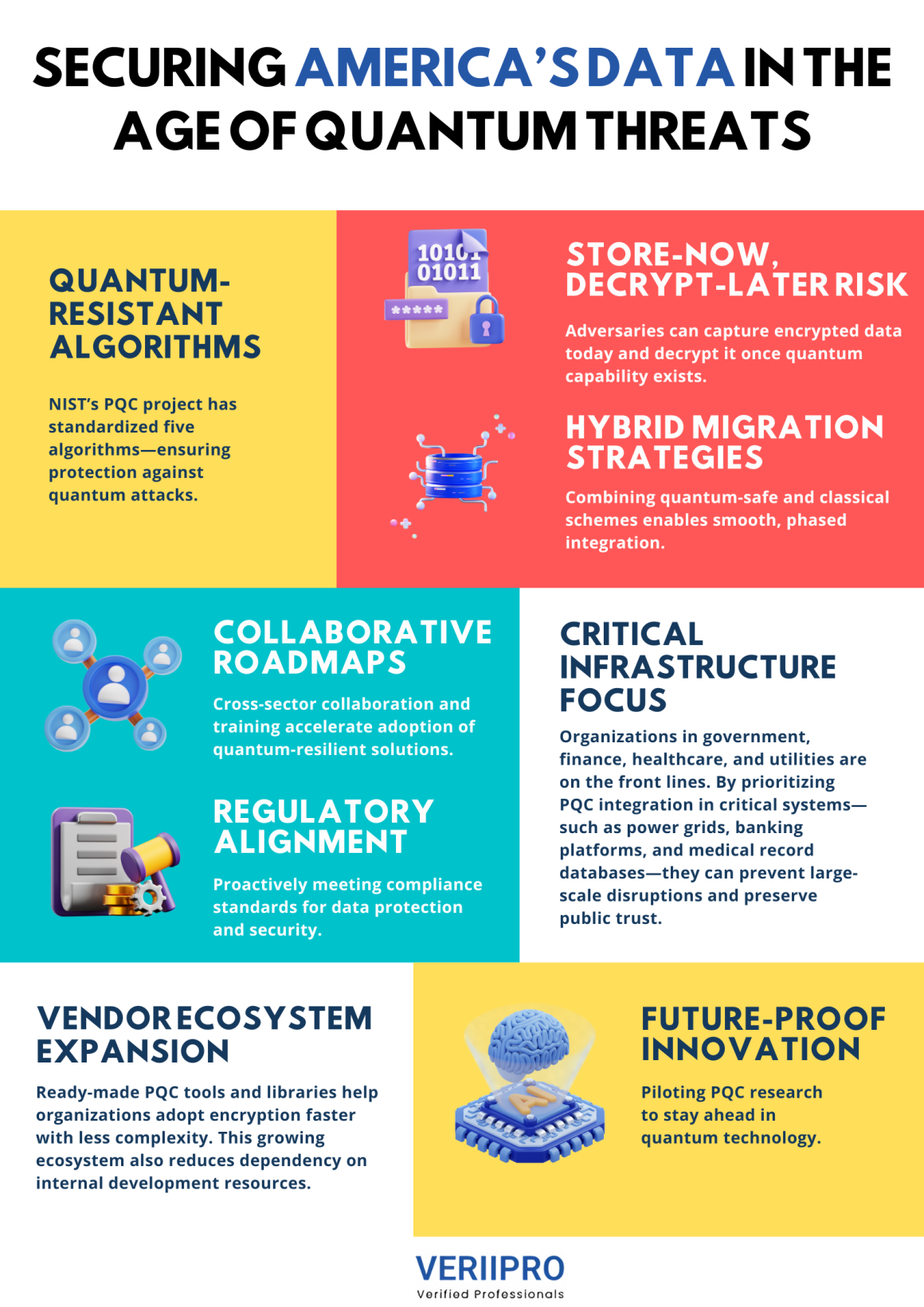
In an era where quantum computing is shifting from theory to reality, traditional encryption techniques face an existential challenge. Post-Quantum Cryptography (PQC) refers to cryptographic algorithms designed to withstand attacks by quantum computers, which leverage phenomena like superposition and entanglement to solve mathematical problems—such as factoring large integers—exponentially faster than classical machines. As national security and commercial systems alike rely on public-key methods like RSA and ECC, preparing for “Q‑Day,” when quantum computers can break these schemes, has become a top priority for U.S. agencies and industry leaders.
The Quantum Threat Landscape
Quantum computers pose a fundamental risk to widely deployed encryption: Shor’s algorithm can, in principle, factor large numbers in polynomial time, rendering RSA-based security obsolete. Organizations handling sensitive or long-lived data—government communications, financial records, health information—are particularly vulnerable, as adversaries could harvest encrypted traffic today and decrypt it once quantum capability arrives. This “store-now, decrypt-later” attack model heightens urgency for quantum-resilient defenses.
NIST’s Standardization Effort
To address these looming threats, the Post‑Quantum Cryptography Standardization project led by the National Institute of Standards and Technology (NIST) has evaluated over 80 submissions since 2016. In August 2024, NIST announced its first four quantum-resistant algorithms—replacing vulnerable schemes with validated alternatives—and in March 2025, added a fifth algorithm called HQC to ensure a diversified portfolio for implementers.
Real-World Readiness and Challenges
Transitioning to PQC involves more than swapping libraries—it demands end-to-end integration across hardware, protocols, and applications. Federal agencies and critical infrastructure providers must inventory systems that rely on vulnerable encryption and develop migration plans before quantum-capable adversaries can exploit them. A recent Thales Data Threat Report warns that “Q‑Day” may arrive sooner than anticipated, urging organizations to accelerate their PQC roadmaps.
Hybrid Approaches and Interoperability
During the migration phase, many organizations adopt hybrid schemes—combining a PQC algorithm with a conventional one—to maintain compatibility and ease transition. This approach allows gradual rollout: new endpoints negotiate quantum-resilient keys, while legacy systems continue operating until fully upgraded. Interoperability standards and reference implementations from NIST and industry consortia play a pivotal role in smoothing this shift.
National Security Implications
Quantum-resilient encryption isn’t just a technical concern—it’s a matter of national security. Adversaries collecting encrypted U.S. government communications today could undermine democratic institutions, disrupt critical infrastructure, or gain strategic advantages once they possess quantum decryption capability. The White House’s Quantum National Security Memorandum underscores the imperative for federal agencies to implement NIST-approved PQC standards swiftly.
Building a Quantum-Safe Future
To secure America’s digital infrastructure, stakeholders must:
- Assess Vulnerabilities: Identify systems reliant on vulnerable public-key encryption.
- Plan Migrations: Develop timelines, budgets, and testing frameworks for PQC integration.
- Educate Teams: Train developers, security professionals, and decision-makers on PQC concepts and best practices.
- Collaborate: Join industry consortia and government working groups to share insights and tools.
As quantum computing advances, organizations that act decisively will transform a looming threat into an opportunity—building trust in a quantum-safe digital ecosystem.
Looking for opportunities in cybersecurity and cryptography? VeriiPro is here to help!









